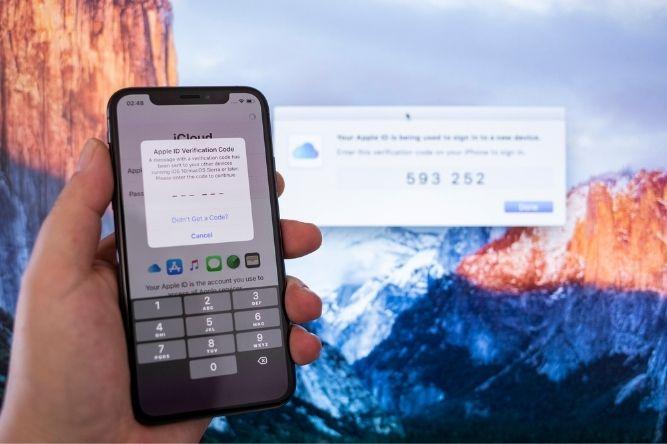
Cybersecurity can be tricky to understand. When you hear about things like Managed Detection and Remediation (MDR) or Two-Factor Authentication (2FA), it’s easy enough to understand that they add levels of security to your network. Understanding exactly how they do that, however, can be a bit more difficult.
Today, we bring you a case study - and a doozy of one, at that. We’re going to look at what happened to Colonial Pipeline - and how MDR and 2FA could have stopped fuel shortages and states of emergency.
The Colonial Pipeline Hack
Colonial Pipeline is the largest pipeline system for refined oil in the U.S. - about 45% of all fuel consumed on the East Coast arrives via the pipeline.
On April 29th, hackers - believed to be associated with the hacking group DarkSide - gained entry to Colonial’s networks through a virtual private network (VPN) account. The account was no longer in use, but was still able to access Colonial’s network.
On May 7th, an employee saw a ransom note - demanding 75 bitcoin (about 4.4 million USD). The note appeared shortly before 5 AM - by 6:10 AM, the entire pipeline had been shut down by Colonial.
The requested amount was paid within hours in collaboration with the FBI. Unfortunately, it’s impossible to determine the extent of the damage caused by cybersecurity incidents in such a short time.
Colonial had to shut down the operation of their pipelines for 5 days. This caused widespread fuel shortages and a spike in fuel prices. Governor Brian Kemp of Georgia and President Joe Biden both declared a state of emergency to allow transportation of fuel by road to the affected areas.
How 2FA could have stopped the attack
We don’t know exactly how the hackers obtained the credentials for the VPN account - though the account’s password was found on a dark net list of leaked passwords. (Just another reason to take advantage of our free dark web scan).
What we do know is that the VPN account did not have 2FA. If it had, it likely would have been impossible for the hackers to gain access to the network. After all, they would have needed access to the account owner’s email - or better still, their cell phone - to pass authentication.
This is “security by inconvenience”. Some businesses are leery about getting 2FA because it can take a bit more time to log in. But what constitutes a mild inconvenience for your team is an insurmountable barrier for most hacking attempts.
How MDR could have stopped the attack
Let’s take another look at our timeline: the attack began on April 29th, when the hackers gained access to the network. The ransomware was executed on May 7th - 8 days later.
There was also a massive data breach - 100 GBs of data were stolen on May 6th, one week after the initial attack.
One week might seem like a lot of time between the network breach and the ransom note - but in the world of cybersecurity, it’s actually astonishingly quick. There are breaches that take months to execute.
Whether a week or a month, most cyberattacks occur in a similar way. Hackers gain access to a foothold - in this case, the VPN account. From there, they attempt to find other vulnerabilities in the network.
To a trained eye, this type of activity looks suspicious - abnormal requests from out-of-use VPN accounts are a pretty obvious tell. With MDR, the network would be monitored 24/7 for these types of abnormal requests - and the account could have been shut down before any damage was caused.
The importance of cybersecurity
Not all of us have companies that control the flow of gas to much of the United States. But there are important lessons to be learned from the Colonial attack.
The hackers weren’t asking for a ton of money, in the grand scheme of things - Colonial has some $3.1 billion worth of assets, and generated a net income of $420 million in 2020. The hackers didn’t destabilize any infrastructure - they probably didn’t have the time or resources to breach any vulnerable control systems.
None of that mattered, however - Colonial Pipeline had to be shut down because it’s impossible to know the extent of the damage from a hack in a short period of time. Customers and business partners had to be informed that valuable data had been stolen. Uncertainty gripped consumers.
Any of this can happen to any business. It’s not just the cost of the ransom - it’s the cost of your reputation. Even small businesses can be affected - hackers don’t care who you are. If they can get a bit of money and some data to sell for very little effort, they’ll do it.
If you’re looking to beef up your security, call our IT company in Winnipeg. We truly believe 2FA and MDR are valuable for businesses of any size - the case study we just looked at shows you why.